



Securing your Azure Kubernetes Service (AKS) deployment is crucial to ensure the confidentiality, integrity, and availability of your applications and data. In this blog post, we will explore some best practices for securing your AKS deployment.
1. Use Azure AD for authentication and authorization . Azure AD provides centralized identity and access management for your AKS cluster. You can use Azure AD to authenticate users and grant them access to the cluster and its resources. To set up Azure AD integration, follow the steps in the official documentation.
2. Enable network security policies . Network security policies allow you to define rules to control inbound and outbound traffic to and from your AKS cluster. You can use network security policies to segment your network and restrict access to certain resources. To set up network security policies, follow the steps in the official documentation.
Here is an example of a network security policy that allows inbound traffic from the Internet to the frontend service, but only if the traffic is coming from a specific IP range:
| |
3. Use Azure Private Link to secure communication between your AKS cluster and other Azure services . Azure Private Link provides a secure and scalable way to access Azure services over a private network connection. You can use Private Link to access services such as Azure Storage, Azure SQL Database, and Azure Cosmos DB from your AKS cluster without exposing them to the public Internet. To set up Private Link, follow the steps in the official documentation.
4. Enable Azure AD Pod Identity . Azure AD Pod Identity allows you to bind Azure AD identities to pods in your AKS cluster, enabling them to access Azure resources securely. This can be particularly useful when deploying microservices that need to access resources such as Azure Storage or Azure SQL Database. To set up Azure AD Pod Identity, follow the steps in the official documentation
5. Use Microsoft Defender for Containers . Microsoft Defender for Containers is the cloud-native solution that is used to secure your containers so you can improve, monitor, and maintain the security of your clusters, containers, and their applications. Defender for Containers assists you with the three core aspects of container security:
- Environment hardening . Defender for Containers protects your Kubernetes clusters whether they’re running on Azure Kubernetes Service, Kubernetes on-premises/IaaS, or Amazon EKS. Defender for Containers continuously assesses clusters to provide visibility into misconfigurations and guidelines to help mitigate identified threats.
- Vulnerability assessment . Vulnerability assessment and management tools for images stored in ACR registries and running in Azure Kubernetes Service.
- Run-time threat protection for nodes and clusters . Threat protection for clusters and Linux nodes generates security alerts for suspicious activities.
To learn more about Defender for Containers, follow the steps in the official documentation
The workload protections dashboard
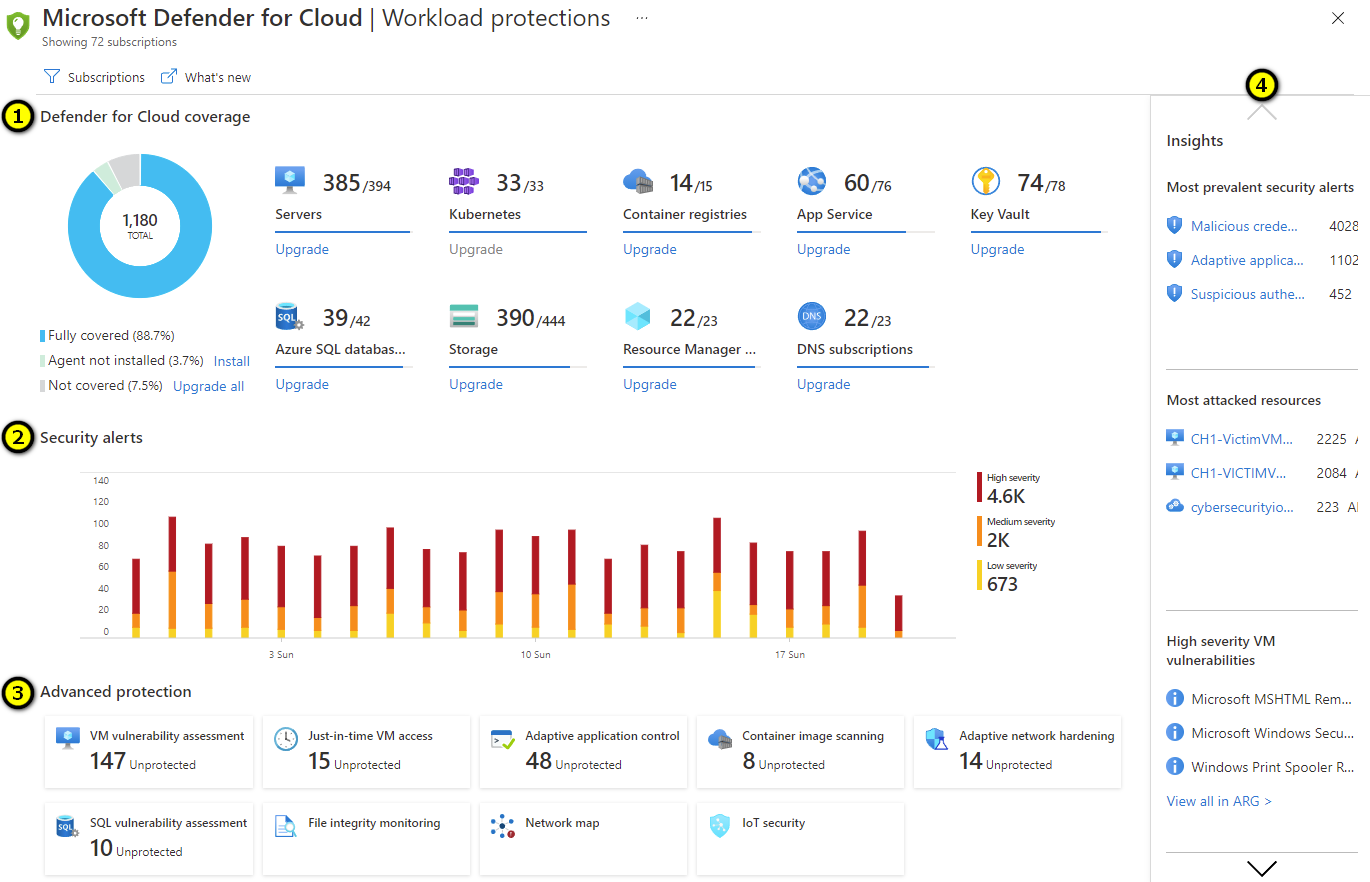
The dashboard includes the following sections:
1. Microsoft Defender for Cloud coverage - Here you can see the resources types that are in your subscription and eligible for protection by Defender for Cloud. Wherever relevant, you’ll have the option to upgrade too. If you want to upgrade all possible eligible resources, select Upgrade all.
2. Security alerts - When Defender for Cloud detects a threat in any area of your environment, it generates an alert. These alerts describe details of the affected resources, suggested remediation steps, and in some cases an option to trigger a logic app in response. Selecting anywhere in this graph opens the Security alerts page.
3. Advanced protection - Defender for Cloud includes many advanced threat protection capabilities for virtual machines, SQL databases, containers, web applications, your network, and more. In this advanced protection section, you can see the status of the resources in your selected subscriptions for each of these protections. Select any of them to go directly to the configuration area for that protection type.
4. Insights - This rolling pane of news, suggested reading, and high priority alerts gives Defender for Cloud’s insights into pressing security matters that are relevant to you and your subscription. Whether it’s a list of high severity CVEs discovered on your VMs by a vulnerability analysis tool, or a new blog post by a member of the Defender for Cloud team, you’ll find it here in the Insights panel.
Case Study
Here is a fictional case study of how a company hardens their Azure Kubernetes Service (AKS) deployment:
Acme Inc. is a software development company that recently migrated its applications to AKS. To ensure the security and compliance of their deployment, they decide to implement additional security controls.
The first step they take is to set up Azure AD integration for their AKS cluster. This allows them to manage access to the cluster and its resources using their existing Azure AD identities. They also set up Azure AD Pod Identity, which enables their microservices to access Azure resources securely using Azure AD identities.
Next, Acme Inc. enables network security policies for their AKS cluster. They create policies to segment their network and restrict access to certain resources, such as the database and storage containers. They also use Azure Private Link to secure communication between their AKS cluster and other Azure services, such as Azure Storage and Azure SQL Database.
To monitor and protect their AKS cluster, Acme Inc. sets up Azure Security Center. They configure Security Center to send alerts for security-related events, such as failed logins or resource access violations. They also use Azure Policy to enforce security standards and compliance, such as requiring secure communication protocols and prohibiting the use of certain resource types.
Finally, Acme Inc. uses Azure Container Registry to store and manage their container images. They use the image scanning and image signing features to ensure the security of their images, and they replicate their images to multiple regions for disaster recovery.
By implementing these security controls, Acme Inc. is able to harden their AKS deployment and ensure the confidentiality, integrity, and availability of their applications and data. They are also able to meet their compliance requirements and reduce their risk of security breaches.
